What Is A Phishing Attack? - All You Need To Know
12/17/20246 min read
What Is A Phishing Attack? - All You Need To Know
Have you wondered what a "Phishing Attack” is and if it’s a type of scam?
In this article we will explore:
What a Phishing Attack is
How phishing attacks differ from traditional scams
Cover examples of phishing emails and websites
Explain the risks associated with phishing attacks, and
Introduce methods of protection for yourself, organization and family from this attack.
By the end of this article, you will understand the basics of a phishing attack and be armed to start defending yourself or business.
1.What Is A Phishing Attack?
Phishing is a cyber security attack which combines psychology, technical systems, security subjects, politics and financial themes. There are many different definitions of a phishing attack or more generally the term “phishing”. This is due to the complexity of the topic and continuous evolution to ensure deception and effectiveness (Alkhalil et al., 2021).
Below are 3 definitions for phishing of varying complexity – From Simple to more Complex:
The Australian Cyber Security Centre simplified the definition of phishing for the public as:
“Phishing is a way cyber criminals trick you into giving them personal information. They send you fraudulent emails or text messages often pretending to be from large organisations you know or trust. They may try to steal your online banking logins, credit card details or passwords. Phishing can result in the loss of information, money or identity theft” (Australian Cyber Security Centre, n.d.).
The definition from the United States Computer Emergency Readiness Team (US-CERT) states phishing as:
“A form of social engineering that uses email or malicious websites (among other channels) to solicit personal information from an individual or company by posing as a trustworthy organization or entity” (CISA, 2018).
Whereas, a more detailed definition from the Financial Cryptography and Data Security text book describes phishing as:
“A form of social engineering in which an attacker, also known as a phisher, attempts to fraudulently retrieve legitimate users’ confidential or sensitive credentials by mimicking electronic communications from a trustworthy or public organization in an automated fashion. Such communications are most frequently done through emails that direct users to fraudulent websites that in turn collect the credentials in question” (Jakobsson and Myers, 2006, p. 1).
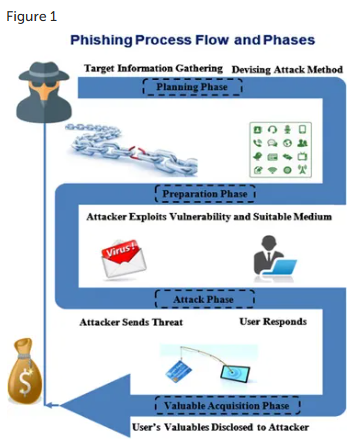
From the paper "'Phishing Attacks: A Recent Comprehensive Study and a New Anatomy” we can simply visualise a phishing attack here:
(Alkhalil et al., 2021)
As you can see, there are many ways to describe phishing depending on the audience and context. Its also likely that the definition will continue to develop as the attack does.
2.Phishing vs Scams
Phishing is a type of scam. The term scam is broader and implies a dishonest method to acquire something of value (Merriam-Webster, n.d.).
If hunting is to scam then, fishing = phishing.
That is likely how the term is coined, scams / hunting can be seen as somewhat predatory behaviour with phishing / fishing being the vector of attack.
Of course, not all hunting is bad, but it does involve a predator and vector of attack.
3.Examples of Phishing Emails
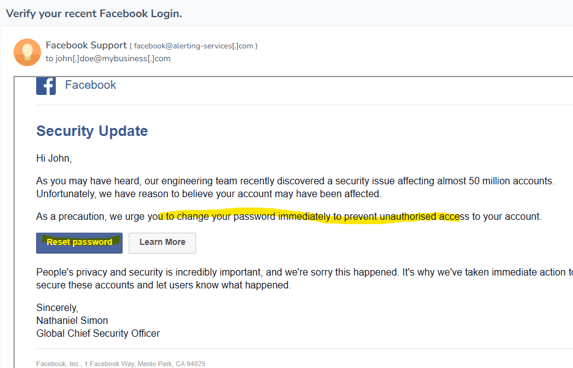
Facebook Password Update – Credential Capture Style Phishing Email Example
Often phishing emails will create a sense of urgency and instil fear so you are more likley to act with emotion and act.
It’s important to think logically and not act in an emotional state when receiving such emails.
Check if this “security update” is factual. Go to Facebook in a different browser.
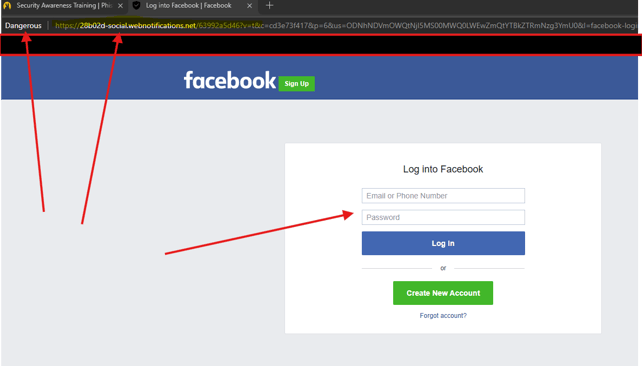
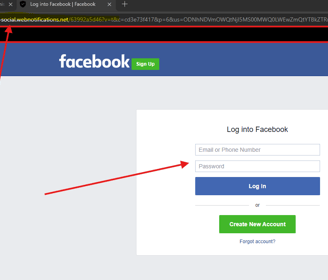
Don't click the link as it will take you to a phishing website page that looks like this:
As you can see, your browser has flagged this page as dangerous, the URL is very odd (different to facebook’s normal URL) and there is a login page. As you input your login details thinking you’re resetting your password because of the above email received, these details will be captured by someone else to be used against you.
This can happened with many types of web applications such as accounting software (Xero, MYOB etc), Payroll Software, Microsoft and more. This is the classic phishing credential capture technique.
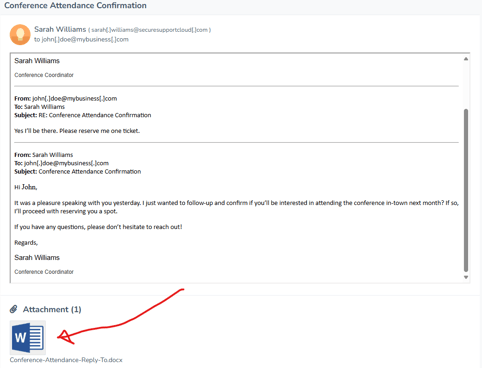
Event Invite With Attachment - Phishing Email Example
Here we have someone sending casual looking messages with an attachment. They look harmless don't they! You might be curious what this event is all about and open the attachment, oh no! That may trigger code execution on your device or install malware.
This type of email looks quite innocent, the sender may even impersonate a legitimate sender or business you deal with. In the worst-case scenario, the attacker may hijack an email account of a business you work closely with then launch phishing attacks from there. This makes the attacks look very legitimate as you already trust the sender.
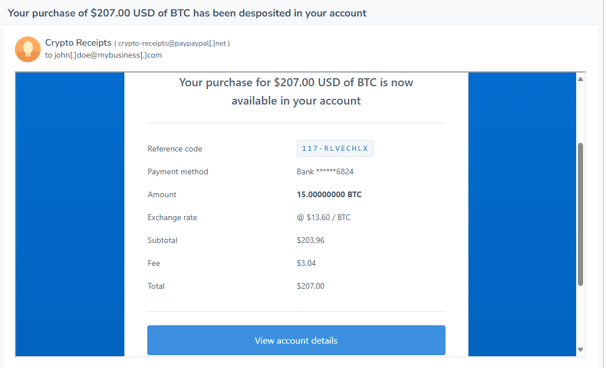
Bitcoin Purchase - Phishing Email Example
In this example your interest is piqued when a financial transaction occurs that you may or (may not) have been expecting. If you are taken by surprise, log into the actual app and check the transaction. Otherwise you will be taken to a page similar our above Facebook Figure 2. example and your credentials will be harvested.
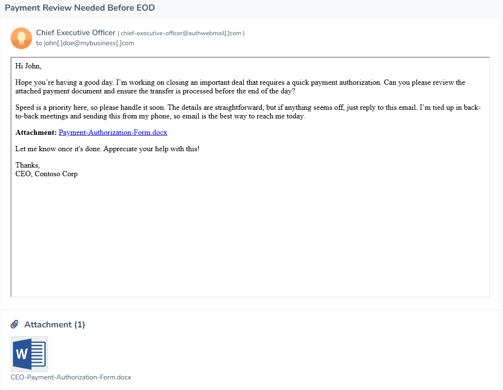
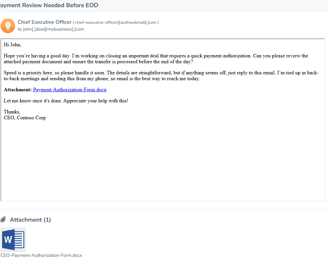
CEO Payment Approval Request – Phishing Email Example
Here we have an attachment with an unusual payment confirmation request. In the haste of doing business, you may quickly glance over this, fill out the required information and send it though. This can be what a “Business Email Compromise” looks like. The attachment may ask you to change details for the payment such as banking information so the payment can be re-directed.
So in this case, have a process in place where you authenticate the payment request by a call. Again you shouldn't be opening odd attachments. Do you even do business with these people?
They could be compromised so have a process in place to double check any payment / banking details change requests.
What are the Risks of Phishing?
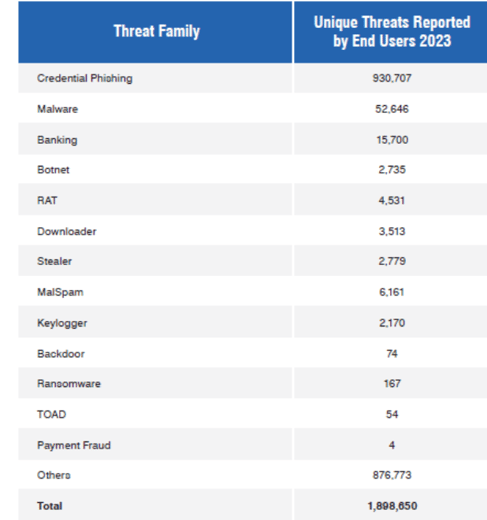
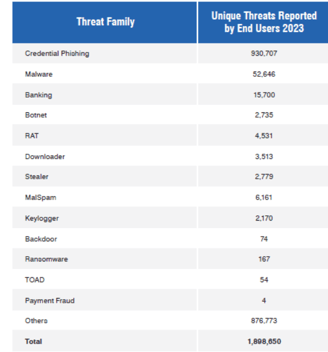
The Proofpoint “State of the Phish 2024” report studied the most reported phishing emails which is broken down below:
(Proofpoint, 2024)
As you can see, the most common type of phishing attacks are “Credential Captures” with Proofpoint users reporting almost 1 million active threats in the period (Proofpoint, 2024).
Furthermore, IBM’s “Cost of a Data Breach Report 2024” found that:
Compromised credentials took the longest (292 days) to contain out of all breach vectors.
On average the second most expensive attack on average costing almost $4.5 USD Million on average for the large organisations they serve (IBM Security, 2024).
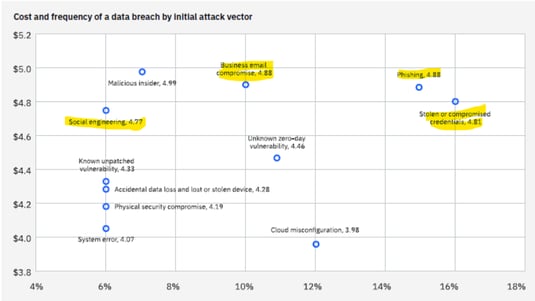
Finally, below is a chart from IBM’s report that shows the costs associated with each breach vector:
(IBM Security, 2024)
As you can see by the highlighted attacks, these are email based and often initiated by phishing.
They are high frequency and high cost.
They involve tricking humans into acting.
Divulging sensitive information
Praying on a sense of urgency and authority
Staying Safe From Phishing
This underscores the importance of:
Phishing simulation training and security awareness for all staff,
Restricting access to sensitive information
Running consistent backups
Isolating cloud environments
Using a password manager
Disabling Microsoft macro use
Maintaining a password policy and;
Having dark web monitoring checking if your credentials are being sold on the dark web.
If you need help with any of this, please don't hesitate to get in touch with the OzSec team using the contact form below.
References:
Alkhalil, Z., Hewage, C., Nawaf, L., and Khan, I. (2021) 'Phishing Attacks: A Recent Comprehensive Study and a New Anatomy', Frontiers in Computer Science, 3, Article 563060. doi: 10.3389/fcomp.2021.563060
Australian Cyber Security Centre (n.d.) 'Phishing'. Available at: https://www.cyber.gov.au/threats/types-threats/phishing (Accessed: 17 December 2024)
Merriam-Webster (n.d.) 'Scam'. Merriam-Webster Thesaurus. Available at: https://www.merriam-webster.com/thesaurus/scam (Accessed: 17 December 2024).
CISA (2018). What is phishing. Available at: https://www.us-cert.gov/report-phishing (Accessed 17 December 2024).
Proofpoint (2024) 2024 State of the Phish Report. Available at: https://www.proofpoint.com/us/resources/threat-reports/state-of-phish (Accessed: 17 December 2024
Cost of a Data Breach Report: IBM Security (2024) Cost of a Data Breach Report 2024. Available at: https://www.ibm.com/reports/data-breach (Accessed: 17 December 2024)



Get in touch
Please dont hesitate to contact us should you have any quetions.
OzSec.
"We help businesses maintain their edge with modern technology."
© 2024. All rights reserved.
ACN 679 706 542
